December 26, 2024 by Jeff Shepard
Collected at: https://www.eeworldonline.com/what-can-be-done-to-prepare-for-post-quantum-cryptography/
Post-quantum cryptography (PQC), also called quantum-safe cryptography, uses mathematical algorithms to create security environments resistant to quantum computer attacks. PQC is a rapidly evolving technology, and preparing for its adoption requires keeping up with developments in several areas.
As part of the formalization of PQC algorithms, NIST has finalized the algorithms and changed their names to fit into the naming convention for the cybersecurity guidelines and standards that the U.S. government and its contractors and vendors must follow to protect data. The three finalized standards include:
- Federal Information Processing Standard (FIPS) 203 is expected to be the primary standard for general encryption. It is based on the CRYSTALS-Kyber algorithm, renamed the Module-Lattice-Based Key-Encapsulation Mechanism (ML-KEM). ML-KEM supports relatively small encryption keys that are easily exchanged and can operate quickly.
- FIPS 204 is the primary standard for protecting digital signatures. It uses the CRYSTALS-Dilithium algorithm, renamed the Module-Lattice-Based Digital Signature Algorithm (ML-DSA).
- FIPS 205 is designed to serve as a backup if ML-DSA in FIPS 204 becomes vulnerable. It employs the Sphincs+ algorithm, renamed Stateless Hash-Based Digital Signature Algorithm (SLH-DSA).
- FIPS 206 is under development to protect digital signatures and will be built around FALCON. It will be called the fast-Fourier transform over NTRU-Lattice-Based Digital Signature Algorithm (FN-DSA).
NCSC recommendations
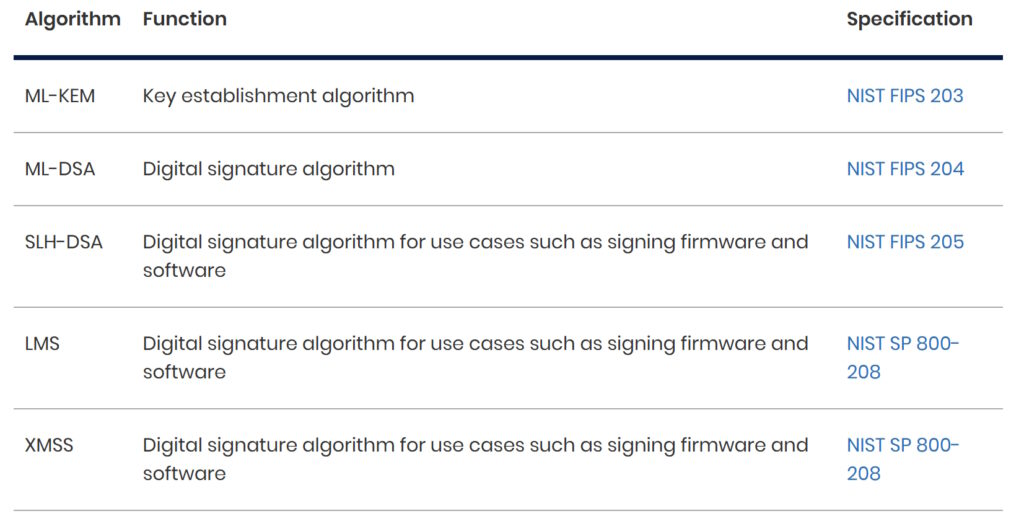
Other organizations closely follow NIST’s development activities, including the Internet Engineering Task Force (IETF), which has been working on updating its protocols to be resistant to a quantum computer, and the European Telecommunications Standards Institute (ETSI), which has been producing migration and deployment guidance. In addition, the UK’s National Cyber Security Centre (NCSC) has developed a set of recommended algorithms, their functions, and specifications (Table 1).
Security and performance tradeoffs
The FIPS algorithms from NIST support multiple parameter sets that provide different levels of security and are suited for different application environments. Smaller parameter sets can be implemented in resource-constrained devices with less computing power and lower bandwidth, making them suitable for edge and Internet of Things (IoT) applications. However, they have lower security margins. Larger parameter sets support higher levels of security but require more computing power and bandwidth to enable larger signatures or key sizes.
Other factors to consider when setting the security level include the sensitivity of the data, its lifetime, and the validity period of the key and digital signature. The highest security is required for long-lived sensitive data and keys that must be protected for extended periods. High levels of security can also apply to digital signatures, where the keys have a long lifetime, like a root of trust.
For example, according to the NCSC, the ML-KEM and ML-DSA algorithms are suitable for general-purpose use. ML-DSA includes parameter sets that meet three security levels: ML-DSA-44 for NIST level 2 security, ML-DSA-65 for level 3 security, and ML-DSA-87 for level 5 security.
The NCSC recommends that ML-DSA-65 can support an optimal tradeoff between efficiency and security for most use cases. ML-KEM-768 includes a single parameter set and provides a similar tradeoff.
Open quantum safe
The Open Quantum Safe (OQS) project is part of the Linux Foundation’s Post-Quantum Cryptographic Alliance. It’s an open-source effort designed to support the transition to quantum-resistant cryptography.
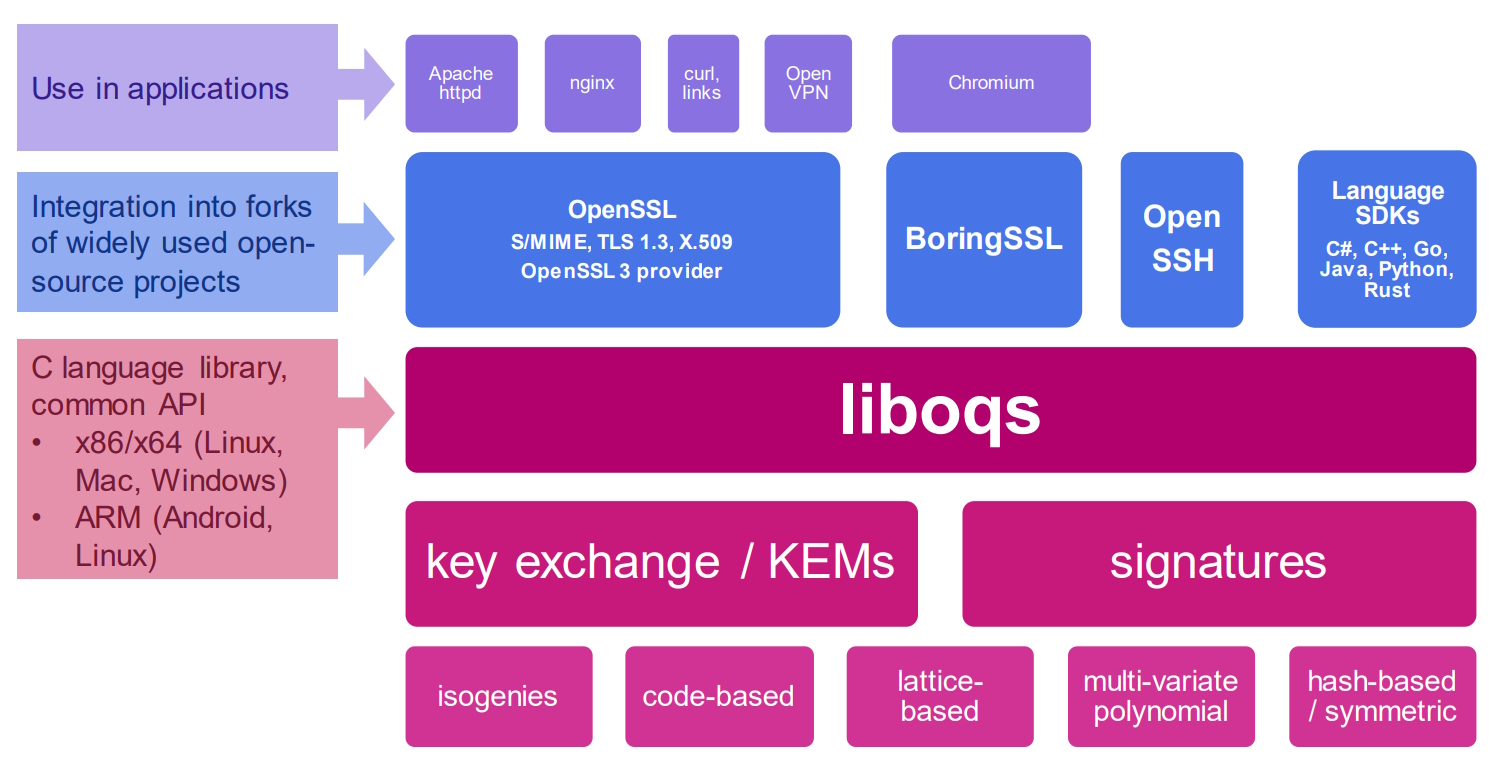
OQS is built on a foundation of various mathematical approaches, including isogeny-based, code-based, lattice-based, multivariant polynomial-based, and hash-based / symmetric cryptography. It supports secure digital signatures and key encapsulation mechanisms (KEMs). The liboqs (a C library of cryptographic algorithms for OQS) are a central element (Figure 1).

Liboqs can be built for use on Linux, macOS, and Windows, as well as on Intel, AMD, and ARM platforms. They include a common application programming interface (API) for quantum-safe algorithms like Kyber, Saber, NTRU, McEliece, Frodo, Dilithium, RainBow, and Picnic and open-source implementations of digital signature algorithms and KEMs.
Other important aspects of OQS include integration into other open-source projects, such as OpenSSL, BoringSSL, and Open SSH, and software development kits (SDKs) for various languages, such as C#, C++, Go, Java, Python, and Rust. Finally, there are prototype integrations and exemplary applications.
Summary
Preparing for a migration to a PQC world requires a lot of work. Fortunately, several organizations, including NIST, IETF, ETSI, NCSC, and OQS, have been developing the necessary tools and refining the options for several years.
References
Announcing Approval of Three Federal Information Processing Standards (FIPS) for Post-Quantum Cryptography, NIST
Next steps in preparing for post-quantum cryptography, UK National Cyber Security Centre
Open quantum-safe,
Post-Quantum Cryptography: CISA, NIST, and NSA Recommend How to Prepare Now, National Security Agency/Central Security Service
Quantum-Safe Cryptography (QSC), ETSI
Quantum-Safe Cryptography—Surviving the Upcoming Quantum Cryptographic Apocalypse, Sectigo
Quantum-Readiness: Migration to Post-Quantum Cryptography, National Institute of Standards and Technology
What is Quantum-safe Cryptography?, Isara

Leave a Reply